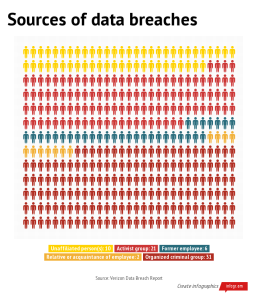
In the available research data, it appears that payment card numbers/data is the compromised in about half the cyber-attacks on all organizations. Here is a list (by ranking) of the data type that was recorded as compromised as a result of a cyber-security breach:
Payment card numbers/data
Authentication credentials (usernames, passwords, etc.)
Personal information (Name, social security number, Address, etc.)
Sensitive organizational data (reports, plans, etc)
Bank account numbers/data
System information (config, svcs, sw, etc)
Copyrighted/Trademarked material
Trade secrets
Classified information
Medical records